SAP-GRC integration: Best Practices to use SAP-GRC for SoD analysis (Risk assessment)
Hello Experts,
Quick: I am wondering how to integrate SAP-GRC for SoD analysis in the best way.
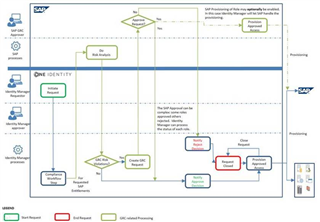
For sure, Identity Managers in-built risk module could be use in order to totally get rid of the need to use SAP-GRC for SoD analysis. However, this will not be achieved short-term. Therefore, I am looking for your experience in how to integrate SAP-GRC in a Request Access process.
By using SAP-GRC WebServices, a lot of scenarios are possible.
e.g.:
Shop roles in 1IM => route the request to SAP-GRC for SoD check => provision from 1IM once status of SoD is “OK”.
Shop roles in 1IM => route the request to SAP-GRC for SoD check => provision from SAP-IDM once status of SoD is “OK”.
Considerations:
- The request passed to SAP-GRC by WebServices (e.g. GRAC_USER_ACCES_WS) has to bundle roles requested for same system. S in case I do shop 2 roles for same SAP system that is SoD relevant, both roles have to be combined in one request (XML) in order get the cross-roll SoD risk checked
- WebService GRAC_REQUEST_DETAILS_WS has to be used rather than GRAC_REQUEST_STATUS_WS as there is always the possibility only one role out of more for same request gets approved
- Is it worth performing SOD check by using WebServices GRAC_RISK_ANALYSIS_WITH_NO_WS and GRAC_RISK_ANALYSIS_WOUT_NO_WS in order to also check user’s full risk in combination of already assigned roles?
Any Suggestions very welcome.
Thank you.
GeKo
ible