In OIM 7.1.2 our workflow is granting business roles to requests that violated policy. After granting the business role, if we run the compliance rule check task, the person will be flagged as violated. Our workflow has several steps, but the last two are: Rule Violations (CR - Compliance check Simplified) then on fail goes to Rule Violation for Exception Approver (OC - Exception approvers for violated rules). The audit policy in question has exception approvers and neither the requester or the requestee is on that list. The work approval history is showing no compliance rule has been violated, however as I stated before, if we run the rule check the person gets flagged as violated. Here is a example of one of the rules that is passes that fails after being assigned:
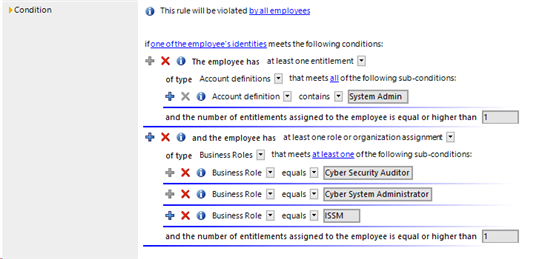
This rule will be violated only by employees that meet all of the following conditions:
Property Business Role is X,Y,Z
If one of the employee's identities meets the following conditions
The Employee has at least one entitlement of the type Account Definitions that meets all of the following sub-conditions:
Account Definition contains System Admin
(IE can't have Role X, Y, or Z and have a role with the account def System admin)