I have been running through setting up an Azure AD connection with a customer, and have hit a snag.
Steps Completed:
1. Joined Starling
2. Set up Connect, and created Azure AD Connector
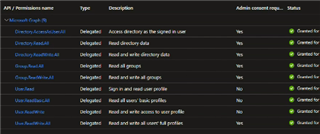
3. Created an App Registration on Azure with the Read/Write permissions for User, Directory, and Group as per the documentation.
4. Successfully tested the Connector on Starling, and added the Registered Connector on SPP.
Now when we try to create an asset, we see Azure AD as an option thanks to our Connector. However, testing the connection gives this error:
AD failed with error: Starling Connect API Failure : BadRequest / { "success": false, "informationMessages": [ "Insufficient app registration roles to complete this operation" ]}. Saving task results. Task completed with failure.
There doesn't seem to be any up to date documentation on what permissions are needed or any roles that are needed. What else needs to be done to get this connection working? Permissions we gave were the following: