Quest Defender is a fast and easy way to bring two-factor authentication to your environment. Tight integration with Active Directory eliminates the cost and time involved in setting up and maintaining proprietary databases. And Defender works with any OATH compliant hardware token, in addition to numerous software tokens, enabling you to select the most appropriate token for your users.
With the deployment time of under an hour, there's no easier way to make your authentication more secure, and your users lives easier. Deploying Defender is one of the easiest things you'll ever do. Simply run the wizard based installer, provide a few simple configuration settings, and you're ready to go.
Defender integrates tightly with Active Directory, and enables MMC based administration. The licensing token and Security Server information is all stored in Active Directory. You can use hardware tokens provided by Quest, or select any OATH compliant hardware token from any vendor.
Issue tokens to users and let them securely assign the token to their account by using the simple self registration wizard like website. Administrators stay hands-off, decreasing the administrative burden, and simplifying token deployment. Users simply enter the serial number and one time password from their token. And Defender enrolls them automatically.
Once enrolled, administrators can manage tokens directly in Active Directory Users and Computers, where a Defender tab is added to each user account. Here, administrators, or help desk personnel can reset user's personal identification numbers, manually assign or unassign tokens, and so on. Defender also includes a wide variety of software tokens, enabling users to utilize their existing mobile devices, including BlackBerry, iPhone, Windows mobile, Palm, Android, and more.
Users can also install a software token on their windows based portable computer, such as a laptop or network. Or be provided a one-time password via email. Software token registration is also entirely self-service, and can send registration information directly to users inboxes. Users simply click a link to begin the registration and installation process.
The software tokens are provided in a self-activating personalized installer. Users simply download and install a small application and they're ready to go. Users can even have multiple tokens assigned to their account without issuing an additional user license. This enables them to sign on from whatever device is most convenient at the time.
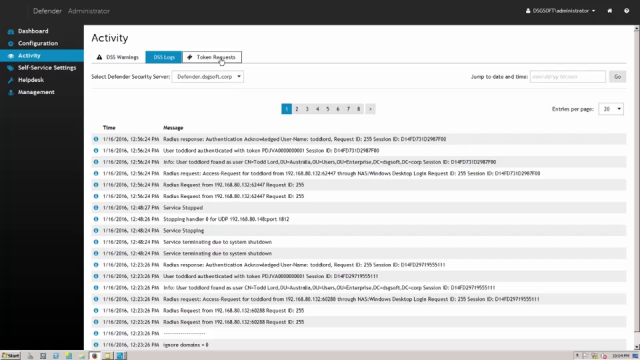
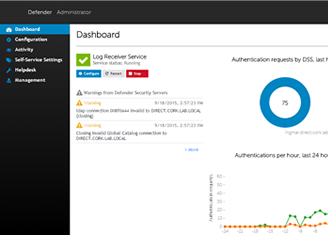
Robust back-end reporting enables administrators and auditors to review user activity, token assignment, authentication statistics, and the entire authentication log. Defender enables organizations to migrate from legacy to factor authentication solutions in a controlled, granular, and staged manner, with virtually no impact on users or existing operations. When user tries to authenticate, if the user is known to Defender, that is defined within Active Directory as having a token assigned, then Defender will handle the authentication-- requesting a token response and responding accordingly.
However, if the user is not known to Defender, then Defender will simply proxy the request via radius to the existing authentication system, which would handle the request in the normal manner. Defender also includes support for advanced pattern based one time passwords. These passwords are easy to communicate to users who need authentication to an application, device, or service-- they're easy to remember and they're difficult to crack using brute force methods.
The user simply remembers their assigned pattern and enters the digits shown in that pattern when they authenticate. Defenders integrated architecture, centralized administration, and easy deployment include support for high availability and scalability through the use of multiple servers. Defender is completely standards driven, enabling you use tokens from a variety of sources. It's flexible, offering customizable security policies and support for both pin and Active Directory password authentication.
Most importantly, users can register themselves. Providing a friendlier, easier, and more transparent migration to secure token based authentication. Quickly and easily add two-factor authentication to your existing Active Directory environment with Quest Defender. For more information, visit www.Quest.com/Defender.
 04:46
04:46