
Continuous Governance to secure your enterprise
Extend identity governance far beyond identities and entitlements to protect/secure privileged access, applications, cloud infrastructure and all your critical data
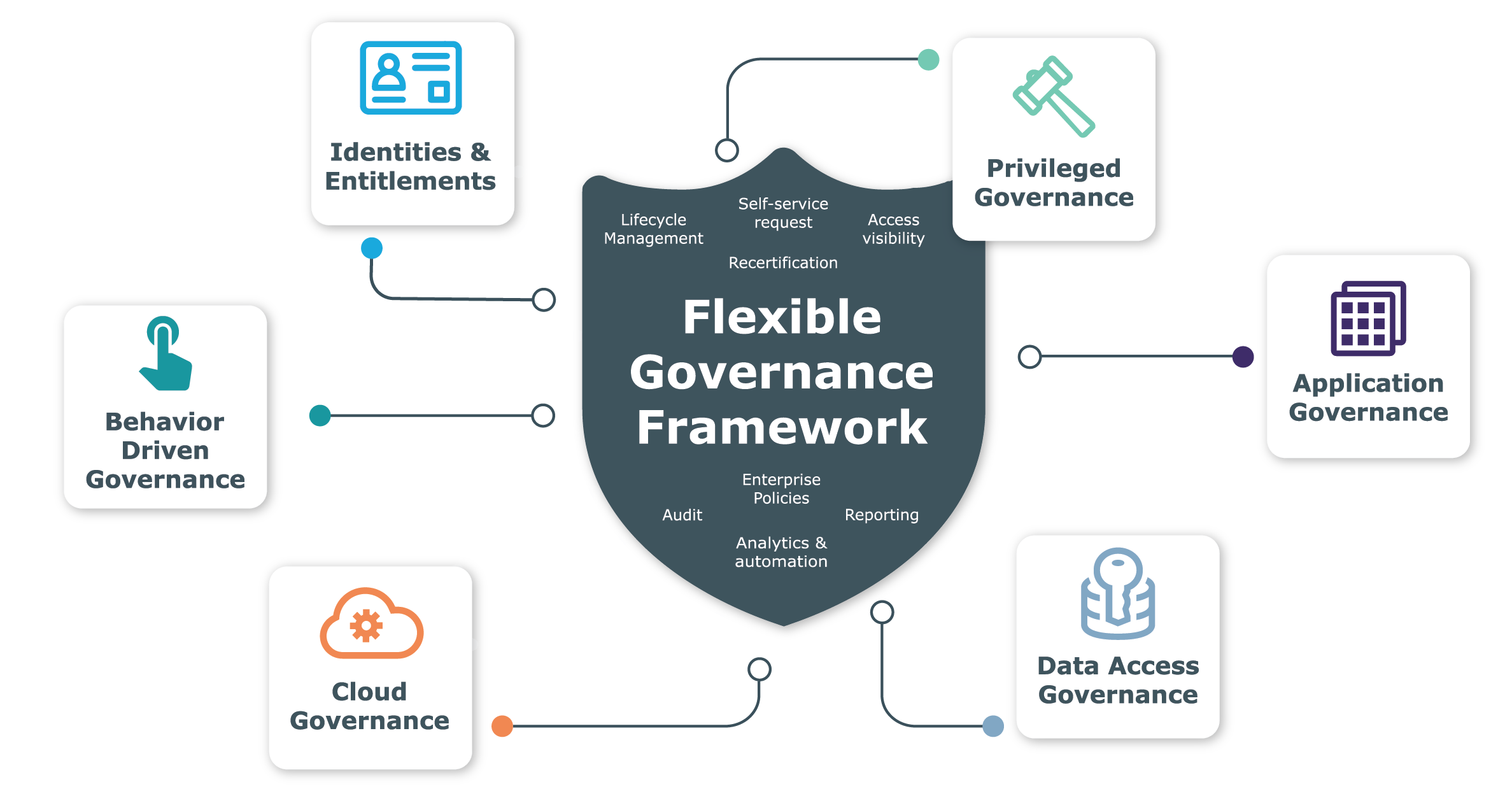
What if you could take your organization’s governance of identities and access rights of users and extend it to protect privileged access, applications, cloud infrastructure and data? What if you had an entire identity governance framework under which you could integrate and manage all your systems? You could extend a comprehensive and efficient identity governance strategy across your entire organization.
Benefits of Continuous Governance
Continuous governance can increase security and protect your organization
Overcome identity fatigue
There’s a new challenge threatening identity processes and systems: identity fatigue. When people are overburdened with identity security-related tasks, they can become overwhelmed and take the easiest route to getting their work done, letting potential vulnerabilities sneak by and leaving users with more privileged access than necessary. Continuous governance with IGA enables you to automate the processes that generally cause identity fatigue, taking human error out of the equation altogether.
Extend identity governance
Security starts with identity. With the traditional perimeter-based security continuing to fade from prominence, protecting your identity data has never been more paramount. IGA includes the processes and approvals required to set up, maintain and certify user access to your organization’s enterprise resources. Continuous governance ensures that the right users have the right access to the right resources at the right time and in the right way – with the right approval and certification.
Behavior Driven Governance
Behavior Driven Governance solution enables organizations to easily enforce the principle of least privilege and reduce vulnerabilities and recertification fatigue, as well as licensing costs associated with underutilized resources. The integration between OneLogin and One Identity Manager gives IT administrators continuous visibility into what access rights are being used and by whom and whether they are being used at all.
Privileged Access Governance (PAG)
Privileged Access Governance bridges the gap between privileged access and standard user identities across the enterprise. Protect and manage privileged access by integrating IGA and PAM technologies, granting an easy 360-degree view of users, accounts and activities. Unifying governance and management of systems enables access request, provisioning and attestation for both privileged and user accounts from a single platform.
Application Governance
Application Governance gives business managers the option to own all or part of the provisioning process, including administering their own policies, roles and access rights. That ownership empowers the line-of-business managers and the business in general. Application Governance delivers control to the business stakeholders who know what needs to get done and who needs to contribute to getting tasks completed.
Data Access Governance
Secure and enable your organization by putting a data access governance tool into hands of the business owner rather than the IT staff. Identity Manager Data Governance Edition provides a self-service portal to manage access to data using an approval, attestation and fulfillment engine, and enables the business owner to grant access to sensitive data.
Resources
Continuous Governance to secure your enterprise
Extend identity governance far beyond identities and entitlements to protect/
secure privileged access, applications, cloud in...
Identity fatigue - the challenge which threatens identity processes and systems
Identity fatigue is a cybersecurity threat with the ability to exploit a flaw in identity processes and systems. What is identi...
2024 KuppingerCole Identity Fabrics Leadership Compass
This report provides an overview of the market of providers of technology for building Identity Fabrics, which are comprehensiv...
Reduce risk and costs with Behavior Driven Governance
One Identity behavior driven governance solution seamlessly integrates the security benefits of access management with IGA so t...