State of the IAM Market: The Convergence of Identity
 24:11
24:11
Related videos

Why traditional IAM tools are now obsolete
What do some of the top breaches in recent history have in common? They were all targeted through identities, despite all having credential-based cybersecurity tools in place. Join Larry Chinksi, SVP of Corporate IAM Strategy at One Identity, for a session on why traditional IAM tools are not enough to protect organizations in today’s ever-evolving identity landscape.
Duration: 21:22

Global insurance company solves the puzzle of Identity Governance and Privileged Access Management
Learn how CNP Vita Assicura S.p.A. overcame the challenges of Identity Governance and Privileged Access Management while optimizing operations and security with One Identity
Duration: 01:31

Seguridad en entornos OT - Uso de herramientas PAM para proteger el acceso a SCADAs
Seguridad en entornos OT - Uso de herramientas PAM para proteger el acceso a SCADAs
Duration: 43:42
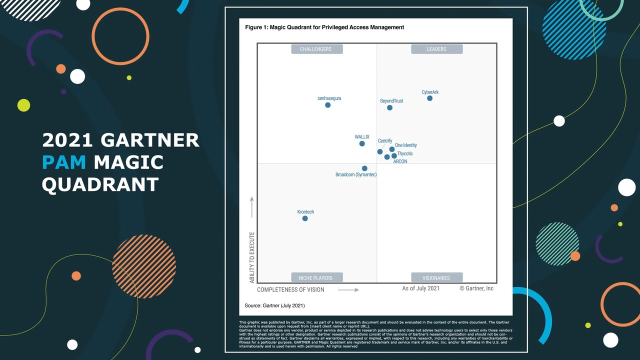
One Identity is named a Leader in the 2021 Gartner® Magic Quadrant™ for Privileged Access Management (PAM)
One Identity is thrilled to be recognized as a Leader in the 2021 Gartner Magic Quadrant for Privileged Access Management. Watch this short video to learn more, and then read the full report to gain a comprehensive view of the PAM market. Read the report: https://www.oneidentity.com/whitepaper/one-identity-safeguard-named-a-leader-in-its-2021-gartner-magic-quadra8150463/
Duration: 01:08

The Robots are Coming! Are you Secure? – RPA and PAM
Robotic Process Automation (RPA) uses robots or digital workers to automate repetitive tasks. While this automation brings new levels of efficiency to all aspects of business, the robots that perform those tasks also invite a certain level of risk, especially when the work they perform involves privileged access. Join Rudy DeSousa, director of sales engineering as he discusses the challenges and risks around RPA and ways to address them.
Duration: 31:23

Work from Home is now the norm, are your most critical digital assets ready??
If you think PAM is just about secrets management you are missing the boat. Next-gen PAM is more than vaulting and you can actually do it pretty easily.
Duration: 33:27

Security Starts with Identity
Protect your hybrid, multi-platform environment with an approach that puts identity at the center of your security strategy. Watch this video to learn how and to see why security starts with identity - with One Identity.
Duration: 01:09

What are the key lessons learned from high-profile breaches?
About 80 percent of cyber attacks and data breaches are connected to privileged credentials. See why your current security practices may not be enough to stop these threats.
Duration: 01:41

What privileged access management practices would you recommend?
You can always do more, learn where you should focus, including two-factor authentication, role-based access and more.
Duration: 01:53

What is the future of privileged access management?
See how PAM solutions are evolving to defend against the ever-growing amount and types of threats.
Duration: 02:07

Why do organizations invest in privileged access management?
Learn about the four primary pain points that drives PAM investments in this video that features a range of industry and organization types.
Duration: 02:19

What solutions has Forrester identified to the privileged misuse problem?
Hear about the two types of solutions that can help solve this insider security challenge.
Duration: 02:14
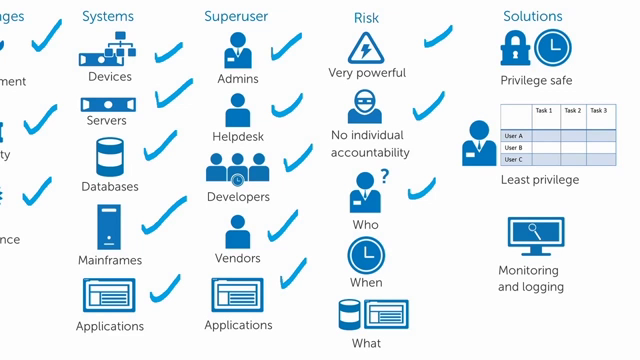
How to control and audit superuser access - On the board
Learn how to take a holistic approach to managing your privileged accounts.
Duration: 07:09
