Hello, everyone. Welcome to our exclusive virtual event series ID:30. Today we have 30 minutes of blazing insights to help you successfully navigate the unique challenges of managing identities in a post-pandemic world. So, ready for some IAM myth busting? Today industry analyst Martin Koopenger will bust wide open some of those tired old misconceptions and share identity program strategies in a session we call IAM myth busting, five things you might think about IAM that just aren't true. Most of you have probably heard these myths. Some of you might even think they're true, but today we're going to peel back the curtain and reveal truth from real world experience and identity industry trends.
Martin Koopenger is Founder and Principal Analyst at KoopengerCole, a leading analysts company for identity-focused information security. Martin has written more than 50 IT related books and is known as a widely read columnist and author. Martin will be joined today by Patrick Hunter, One Identity's Technical Sales Director for EMEA, who has over 25 years of working with many organizations to successfully implement secure IAM solutions. This is the most IAM fun you can have without an explosion. Welcome Martin.
So thank you very much, Lorene, for that introduction. So I'm Patrick, if you want to know which of the two is which, and welcome to this. This Is the series of the ID:30 program that we're running here for One Identity. So thank you for joining us today. Also thank you very much to my esteemed colleague over here, Martin Koopenger for agreeing to be a part of this particular program. So welcome Martin.
Welcome.
So what we're going to do is kick straight off. Let's bring up that first myth if we can. So the first one I want to discuss, Martin, is IAM is all or nothing. I think that the basis of this one is around, I have to do everything, all in one go, it's a Big Bang approach. It's quite over facing, but that's what identity is all about. Do you got any comments on that?
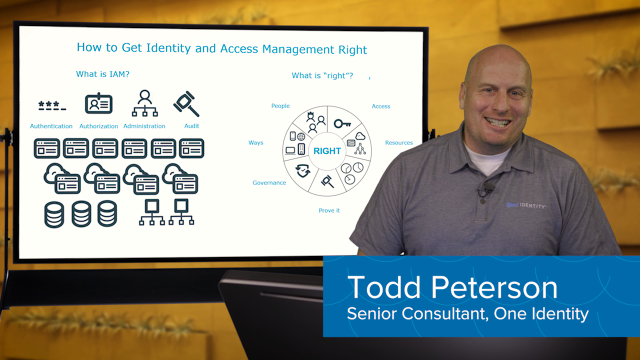
Many, I would say. So the first one is, when you look at IAM, they are broader and more narrow definitions, but all of these definitions are IAM is not only IGA. There is provisioned access management, there is Webex's Federation, and now depending on the definition, might be far more elements. So saying it is one, doesn't really fit to what identity management is about. It's about a number of different themes and so if you look it up, it means there must be multiple approaches and you need a program.
OK, so we're looking at more of a modular approach usually?
So my recommendation is start with a perspective, a bigger picture of what you want to do in IAM, so you need to have a vision, a mission, but you also need to have a plan and a blueprint. And that is not a year-long rocket science project, it's setting up a program identifying the major areas prioritizing. That is where you should start, because if you start with the individual approach and say, Oh I do that, then you might go in the wrong direction and you might end up with a lot of challenges in integration and again getting budget. So if you have a program, a lot of things are better to handle.
OK, so essentially, it's start with a plan, know where you're going, and don't eat the elephant all in one go.
Yes, I think slice the elephant and have a plan, have a program. Because this program should define how you transfer from project to the line organization. It also should define how a line organization looks like. I still see many, many organizations which have a too small, too, I would say, immature IAM organization needs, depending on the size of the organization, you need to have some sort of an IAM organization. All that should be part of the planning and bring up this standard saying, you don't construct the house without having a blueprint. And you shouldn't construct your IAM without having a blueprint, and that helps you to also, as I've said, prioritization and having small growth tracks which allow you to succeed instead of having a multi-million budget maybe and failing because you just try to do too much in a single step.
OK, so that's all that's our myth busted there then. So it's interesting, a lot of our customers, we see them and some of them are on different levels of their maturity. So we try and guide them that way and I think, obviously, it's pretty much the same for you there. It's perfectly OK to start somewhere and just build out from there. OK, brilliant, so I think the next myth we're looking at here is, it all sounds great, and what you've just said is perfect, we've said we've got a plan, it's in place, but I can't. And there's always a reason, whether it's a CIO reason, like it's cost, it's time, it's the complexity. Shouldn't we be concerned that this myth is around that people can't do this?
It is a [INAUDIBLE]. The good thing-- or the good news maybe is that it's less a problem than maybe 10 years ago to [INAUDIBLE] for IAM. And the problem, I can't, frequently comes from surface [? big ?] selling IAM the wrong way. So when I go back into history, identity management started as an administrative tool, so something which promises to improve efficiency for administrators. OK bring in some more convenience for users with single sign on, but the next big driver was compliance. So when the Sarbanes-Oxley act became relevant, some more than 12 years ago, a lot of projects were driven by that, but administration efficiency is not a very compelling argument, because if you say, we save money-- Yeah whenever, when does IT ever save money? At the end it's yes, sometimes it works, but it's not a very compelling argument. And governance is just a negative driver, so we have to do it.
But if you look at the role that digital identities play today for the digital transformation and the role identity management place for efficiency in your business at all levels from working with employees, partners, customers, to [INAUDIBLE] things, then there is a positive element in that, and that is what is increasingly understood by the C-level, and that helps in [INAUDIBLE]. But it's very clear, If you want to do identity management, go beyond the technical and tech compliance aspects, and educate people about the business value of digital identities and IAM.
Well that sounds actually perfect. So it's a combination of just evolving stakeholders. I can't-- some people have different priorities. I mean obviously people are concerned about breach a lot these days. GDPR is a little bit of revenge, right, on SOX. All these things are going to be front in mind. So what's your opinion about the role of the Auditor in identity and right now, in this particular case? I can't, but people have been audited so--
Yeah, so the Auditor is your best friend, in some way, for many years right now. But you need to be careful, because again, if you just do it because of the Auditor, that's the risk that you do a project to just satisfy the audit requirements. And so you get your check-box compliance, but there might be a lot of things you could have done better with little extra effort. So you will be also the situation that went to the audit requirements change and they are changing always, that Europe, again, have to do something. So you always are trying to catch up with the auditors, which is not a very smart strategy.
The smarter strategy is to say, we get in a position where we are pretty sure that we can satisfy the needs of the auditors, but also work to the business. So auditors help to get things started, but you need to think bigger than just for check-box compliance.
OK, all right, fair enough. So it's not a case of I can't, it's a case of I have to, so that's another myth I think busted there.
Yes, it's maybe even a little bit more than I have to, it's I should. It helps my business.
All right so brilliant, myth busted. It's not a case, it's not an option. I like that. OK the next one, takes us a slightly different path, Martin, so I've got single sign-on, which it sort of indicates that I have consolidated my identities. It's that I have one master identity. I'm done, I'm finished, that's good enough. I've got control over the user, that's Patrick Hunter, I can log in and do my stuff. Is that really true?
No. I'm going to go back to the first myth. Obviously it isn't true, because IAM is more than authentication, modern single sign-on, there are many elements. But a good user experience is important, and single sign-on is part of a positive user experience. Single sign-on combined with strong, but still convenient authentication, is even better, because then it combines usability and convenience and security. But then you used to say, OK, wow, cool, I can have my single sign-on and then they end up saying, Oh, but where do I request my access, or they end up with these complex access reviews we find sometimes today.
And they learn to churn. Churn is not at the end already, and so single sign-on is a good quick win, but you always should, when you do projects, think about-- what are my quick wins in every part of my program? And what are the big wins, what are the big improvements such as reducing the time, to well you for digital services such as being ahead of the Auditor, et cetera. Improving cyber security at mitigating at risks of attacks for highly produced [? records, ?] all these things should be defined as big wins, but also the quickness. SSL is a cool quick win, but it's not enough.
What I'm hearing, actually, well I suppose here, I suppose the thought is, user account is all well and good, but it's the underlying infrastructure accounts, those generic accounts, that could be actually the point really left exposed.
So every targeted attack-- so we have these mass attacks which just send out phishing mails to millions of people and stuff like that, that's one part. But then there are the targeted attacks. These are succeeding such a mass attack for the ones who fall victim to the phishing attack, are really targeted at a certain type of business or governmental organization. Targeted attacks always are after the highly privileged accounts after-- every type of account, be it an admin operator, a system account, or others which have-- or technical accounts-- which have relatively many entitlements, because they are the ones where you can sort of run the most successful attacks in the sense of you achieve what you want to achieve, destroy, steal, whatever.
Right, so what I'm hearing is, single sign-on-- good for the user, good user experience-- is the beginning of something, but actually it's just a layer on top of what's really critical, is the infrastructure underneath and those accounts. So I think that's another myth busted there, I think. So with all of these approaches, I'm hearing all the way through so far-- maybe we'll hear the same as we continue-- Although you have to look at all the different facets, all the different facets, all the time with the stakeholders.
OK brilliant. So if we move on to the next one-- So look, we've established it's important. We've established that identity and access management is as a should, maybe more than a can't, but right now I've got other priorities. I've got other priorities in the business. Identity can wait. I think we hear this quite often is, it doesn't matter-- the active directory might be in a bit of a state. I may have groups that I didn't quite know what they're doing. I've got a few orphaned accounts, but it's OK. We've been working quite happily like that for some time. So I'm going to go and do other things. What would you think about those sorts of things that we hear?
So my first question would be, what would be these other things that have a higher priority than the digital identity, then being compliant? That could be the somewhat provocative first question, but that doesn't really help. But if you look at-- don't you need a strong identity management for these other things you want to do? That you are at this business [? enabler ?] discussion. And I think that would be probably the first response to, I have so many other priorities. I can't do identity access management, outside of what we talked about before. So that would be the way I look at it.
I would start into this discussion. At the end you need to make a list of priorities for your overall IT and what you do in security and identity management. But if you-- So we frequently do that, for instance, for a cybersecurity tools portfolio optimization, so you have a [? zoo ?] of tools. And what we compare, for instance, is the cost versus the risk mitigation. And I can't guarantee IAM always is pretty much the upper right corner being very helpful to risk mitigation and still being acceptable in cost. If you do it right, it's not cheap, but it's affordable, if you do it right.
I'd like to ask the audience, if I may, a question. If you could respond in the chat with just a 1 or a 0. 1 for yes, 0 for no. In your organizations, is identity a priority right now? So if you start putting those 1s in for yes or if you're finding it's not a priority for your organization, put a 0. Just a quick poll, I'd be really appreciative if you could do that for me please. So security for a lot of people starts with the identity. The identity itself is the fundamental building block of what people are trying to find to attack.
What's the important thing about protecting against a breach? You talked about phishing. What other things can people do to sort of try and secure that identity from being taken over?
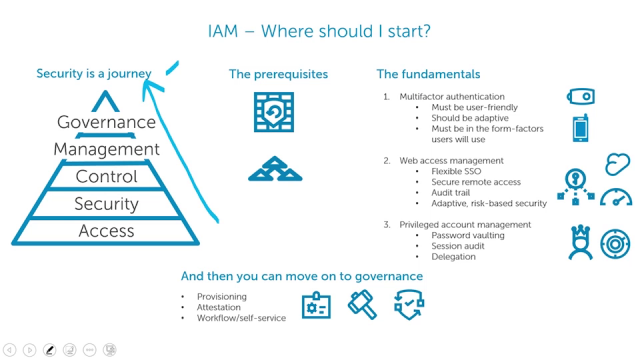
First I am fully with you, because identity management, at the end, is about who has access to what. And if we are about protecting, it's about avoiding malicious access some way or another. And so that access part always is in, and the who part is also important, because that's the combination. So the first step, from my perspective today, is ensure that you have MFA turned on, multi-factor authentication, because this is-- I wouldn't say a no-brainer today, but it's something you can do rather easily based on software products you procure, but also some technology anyway have with some of the services you might have.
If you do that right, you did an important step, because that helps against phishing, to some extent, because if someone has done phishing the username and the password, still the second factor is missing, and that makes life for phishing, for attackers using phishing attacks far more difficult. So that's the starting point.
Perfect. OK, I can see from the polls here, actually, for most of our customers here or people in attendance is that it is a priority, and rightfully so. I think identity is a part of security as a whole. We've seen time and time again, front page news, we see the breach, we see the fines with GDPR, where people are actually-- there's actually some teeth now, where as before-- Maybe this goes back to one of our previous questions, where I just can't right now, it doesn't matter. Audit combined with GDPR, with socks, with everything else, there's a real reason to make these changes, right?
Yeah and I think they're great examples from just, I think last week it was, with the Twitter incident.
Right,yeah.
So that was very much about, should all these people have that much access or all these accounts of these people have that much access to so many different accounts, So much sort of high risk accounts? And if you look at that then there obviously was a lot of-- identity and access management could have helped mitigating some of the things in that.
Right. Speed bumps to the hack. All right, so OK, well I think that's another myth busted there really. The priorities are, and I think we're seeing common sense here, is from an IT point of view, if you can't protect the asset, then you might as well just open your doors, job done. So the final myth I want to bring up today, and this one is common, I think, is the future with IAM does not include my legacy systems. I think that with the world turning to the cloud, people sometimes lose track of the fact that fundamental systems are running in their background, whether the Unix, Mainframe, AS400, and actually on premise, AD as well is falling into this category now. How important is it to encompass everything in our strategy?
I could say it depends on. So if you manage to shift everything to the cloud, so not only by lift and shift, but by a full migration, fine, then you don't have to like our systems anymore, but reality is different. Look at insurance companies. Many of them still have a mainframe. And look at manufacturing companies, they always will have IT on their factory floor. Look at many of the cloud strategies, they just start, maybe they start two or three years ago, it's still a long way to go. And much of what happens is just to lift and shift.
So the legacy application runs in a different data center, which is called Cloud, but it's still legacy applications. So if you want to succeed, you need to have a strategy for hybrid reality of your business and your IT.
OK, so they can't be excluded, but should they be considered a weak link, these legacy systems? How do we manage this?
I think there are different ways. So on one hand, some of the identity as a service solutions are relatively good in connecting back to on-premise systems. The other thing you might consider is saying OK, I construct my future IAM infrastructure, so we call it identity fabric, and that identity fabric then is where I want to be in the future where I'm heading. So one of the target systems-- So some systems are connected to that, what works easy and some of the-- one of the other target systems is trust your legacy IAM so to speak, in quotes, which has the connections to all your legacy IT anyway. And then you can gradually shift until you don't need that anymore.
So there are various ways to play it and this needs to be analyzed per customer, because there is not a single right answer. But you have plenty of options to deal the steps, so modernizing your identity management without losing the connection to what you need to protect, because legacy-- take a mainframe at an insurance company. That is something you still must protect. There is no way to audit.
Absolutely. All right, so what I'm hearing, holistic approach, think about everything, an identity is an identity, doesn't matter where it sits, or what it's used to access. OK, so that's another myth busted right there. So before we move onto the next segment, I just wanted to ask you, Martin, what's the most common thing that you're asked right now? Which maybe it's myth-based, maybe it's not, but what's the most common question that you're given by your clients right now?
Honestly, the most common question is what is the future growth of Microsoft Interactive Directory? Because it pops up everywhere, that is a very common question. So how does this fit into the entire picture? And so we get this question very frequently. We get another question is, how does IGA plays with IT service management? Also very frequently asked these days and we see a lot of Demand around this entire distrust of this entire-- How do I modernize my IAM or shift my IAM to support my cloud-first strategy, and what is the right way to do it?
All right, perfect, thank you for that. So what we're going to do now, what I'm going to do is ask our audience, if they have any questions-- we're going to watch a little segment of tips in a second, but ask the audience if they've got any questions, type them in and there's a little checkbox to the side to mark it as a question. If you could do that whilst we hear from Megan talking about some of the things that we could do to improve our security footprint. So over to say Meghan.
Here are five tips that will set you up for success with your IAM program, and help you avoid the pitfalls that normally stand in the way of IAM success. Number one, start where you are going to have the biggest impact. IAM is many faceted, and can be a really big undertaking if you choose to attack it all at once. That's a sure path to failure. Instead, I recommend that you look at the whole of IAM, and choose the one thing that will get you the biggest impact the quickest. If that's making users' lives easier with SSO, go for it. If that's increasing security by unifying and automating provisioning, do that. If it's addressing the high risk of privileged accounts, cool. Or, if it's just solving the problems of one key system like Active Directory, do that one.
Either way, once you solve the first problem, you move on to the next, and then the next, and then before you know it, you're very far down the road. Number two, give yourself some credit. Something is better than nothing. A lot of people view IAM as big bang, all-or-nothing undertaking. As I just mentioned, you can't solve all the problems at once, but you can do some good. And be sure to celebrate your victories, even the relatively small victories. A win is a win, and you can't take the title until you've won enough of the regular season games to qualify for the playoffs. Embrace the journey and recognize that you are doing some really great things.
Number three, without IGA and PAM, SSO doesn't matter. Single sign-on, or as the industry calls it, access management, is the most visible aspect of IAM, but even the sexiest SSO program is useless if the underlying identity governance and administration foundation is broken, or if your privileged accounts are out of control. So of course, do access management, it's important, but don't assume that it's enough. IGA and PAM are even more critical and even more impactful.
Number four, go for the quick win. While the technology battle in IAM is important and you can solve the problems with almost any solution, if you have enough time and money, perhaps the most important battle is the political one. Nothing derails an IAM program faster than lack of executive buy-in. Make sure that your program has well-defined, achievable, and highly visible milestones, that will show your executives that IAM is delivering value and making a real difference.
And number 5, don't ignore the legacy systems. Just because something is old doesn't mean that it doesn't need IAM. Don't be distracted by the shiny new things like the cloud or RPA when there is a cesspool of broken sitting right behind you in your legacy systems. IAM in all its flavors is critical to the entire enterprise and must be implemented on each and every system in the enterprise. Just because you're moving to Azure doesn't mean you can ignore your on prem AD.
IGA and PAM must be applied equally to all systems, not just the sexy new ones that are getting all the attention. You're just one breach away from your legacy system suddenly being the hottest item on your plate. And that wraps up the five strategies in this ninja tip.
Thank you Megan for that. So I think what we've heard over the last 30 minutes, Martin, if I just quickly summarize-- All those tips kind of match, I think, some of the things that you told us, but it's approach things with a strategy. Have a plan. Know your stakeholders. And that's if you've already got the project going. If you're thinking about starting a project or you haven't started a project yet, it's time just to probably get on board and start thinking about those projects.
You know if I was just to ask one last thing before we wrap up, Martin, I've asked you before, what's the most common thing you hear. What's the most common piece of advice, though, that you give to people? What's the first thing that you say to everyone?
Yeah, at the end it's what you just said. Start with a plan. Start with a picture. So we frequently start with a bench-marking to look at where do you stand, where are the gaps, and from there understand where to set your priorities. I think priority-setting probably is the most important thing at the end if I would nail it down. The [INAUDIBLE] other things, but at the end it's priority-setting to understand which steps to do in which order.
OK, brilliant, well OK, with that this wraps up today's session. So thank you very much, Martin, for agreeing to answer these questions with us today. Thank you everyone for joining us. We hope it's really useful and we hope that you'll join us for the future ID:30 sessions coming up, so look out for those. So with that, thank you very much everyone. Enjoy the rest of your day, and thank you again Martin. Take care everyone.
Thank you.
Bye bye.
 31:30
31:30